What is Phishing?
Phishing is a type of cyber-attack that uses deceptive emails, text messages, or websites to try to gather personal information, such as account credentials, financial details, or any other sensitive information.
Most of the time, the person behind the phishing content is presenting as a reputable company (banks, universities, etc.) in order to trick people to give them their information.
Ways to Spot & Analyze Phishing:
🐟 Be cautious with email links and attachments, especially if you do not know who it is coming from.
🐟 Verify the sender’s credibility by double checking the email address, and cross reference it with known and trusted contact information.
🐟 Be aware of emails sent from external senders, or from addresses outside of the university/organization.
🐟 Scrutinize all email content. Look for grammar/spelling mistakes, unusual requests that involve sensitive information or requesting money in any way.
Examples of Phishing:
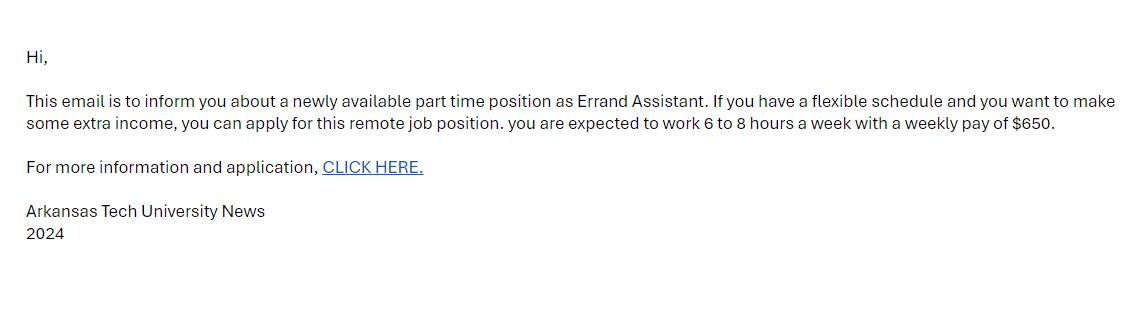
🐟 Email:
- The offer is too good to be true.
- The greeting and salutation is to informal for a university.
- The link is ambiguous with little information about the proposed “opportunity.”
🐟 Text Message:
- The attacker is pretending to be Arvest Bank.
- There is a sense of urgency to click the link.
- It does not address the client by name, but instead uses the generic term, “Client.”
- The link is suspicious.

If You Are Unsure…
When in doubt, ALWAYS err on the side of caution! You can always reach out to the Campus Support Center at (479) 968-0646, or visit RPL 150, to verify the legitimacy of any suspicious emails you receive.
Essential Guidelines
The “golden” rule when it comes to dealing with phishing is to NEVER give away any information to the attacker, even if you’re still not sure if it’s legitimate or not.
Sensitive Information Includes…
🐟 Personal information:
- Social security numbers
- Addresses
- Phone numbers & other emails
- Date of birth.
🐟 Financial information:
- Debit card information
- Credit card information
- Bank account information
🐟 Account credentials:
- Username and passwords
- Security question answers
- Sending out your Duo code
Attacker Tactics
Reputable organizations will almost never request sensitive information over email, especially if the request is unprofessional, unprompted, and urgent.
Attackers often create a sense of urgency, tricking you into acting fast to claim a reward or avoid a bad situation. Before you click the link, pause and scrutinize the email.
If you do get to the point of inputting your information, check to make sure the URL of the website is credible and matches the organization requesting information from you.
Multifactor Authentication
Having a second form of account verification is a cyber security industry standard. Here at ATU the multifactor authentication we use is Duo.
Every time you request access by logging in, you will either approve the push notification through the app or type in a one-time code from the app or a text message.
Some attackers will try to ask you for your code alongside asking for your username and password so that they can verify themselves when accessing your account.
Duo Guidelines to Remember:
🐟 Only input your Duo code in the Duo prompt when logging in. You will never need to verify your account by putting your Duo code into any other application.
🐟 Only approve a Duo push you requested. If you receive a push you didn’t request, it’s likely your account has been hacked. If this happens, consider changing your password.
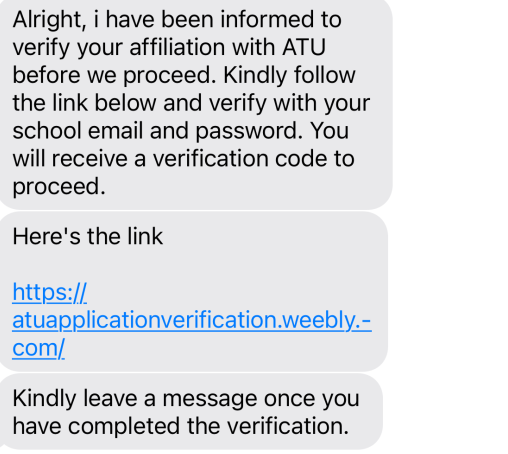
Duo Phishing Example:
- Notice there are grammatical errors in the text.
- The link that was sent is suspicious, look out for “.weebly.com” addresses, or similar URLs.
- They ask for the verification code, which in this case would be a Duo code.
Reporting
If you receive a suspicious email or text, report it to Campus Support immediately! That way, Campus Support can make sure not only you are not affected, but other people are not phished either.
To Report Phishing to The Campus Support Center:
🐟 Call Campus Support at 479-968-0646
🐟 Visit the library at room 150
🐟 Forward the phishing attack to campussupport@atu.edu
You can report an email as phishing in your Outlook inbox, however that does not notify Campus Support, it only flags it for review for Microsoft.
Don’t take the bait. 🎣
Thank you for your help keeping ATU cyber safe!